Vulnhub: JIS-CTF VulnUpload Write-Up
This is a writeup of JIS-CTF: VulnUpload VM from Vulnhub.
Challenge: There are five flags on this machine. Try to find them. It takes 1.5 hour on average to find all flags.
Difficulty: Beginner
Date release: 8, Mar, 2018
Author: Mohammad Khreesha
Write-Up
Getting IP address:
I was able to run this on vmware even though it says on the page only working with virtualbox.
I configured the VMs (attacker and target) in host-only network, my host-only network has the IP: 192.168.199.0.
On running nmap:
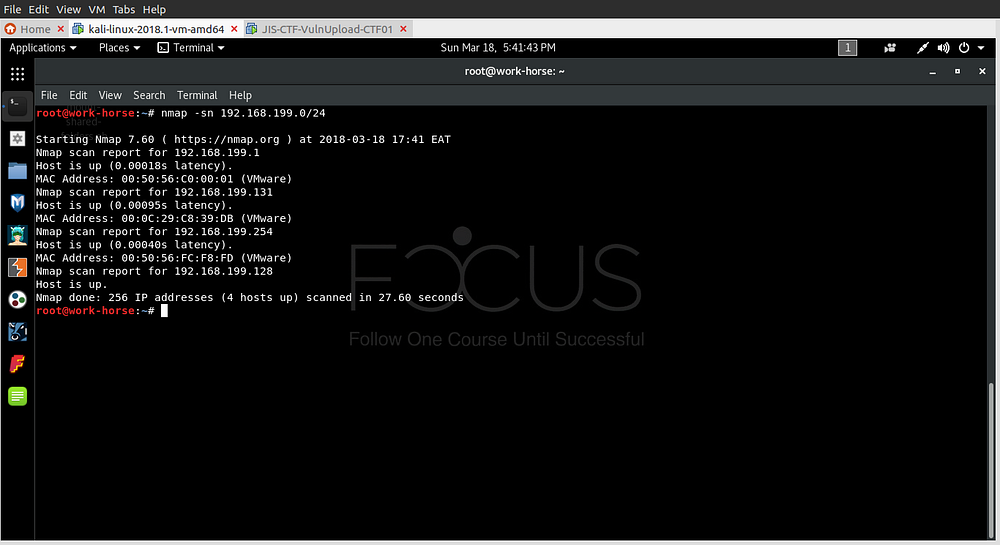
I found the IP to be 192.168.199.131, this is the result on a browser:

Information Gathering:
I decided to run nikto and see what useful information I would get:

It found several directories and also a robots.txt file.

After loading the robots.txt file, I saw one of the directories listed is flag.

After checking it out. Boom! Our 1st flag!!
I did some exploring on the other directories listed on robots.txt file but most displayed nothing except the /admin_area :

The page just displayed “The admin area not work :)” but on inspecting the page we find our 2nd flag!! commented out. There is also some login credentials.
I tried login with those credentials and got a successful login:

Exploitation:
For exploitation I decided to try uploading a php-reverse-shell file which can already be found in kali, I copied mine to desktop and renamed it to exploit.php:

I edited ip to my attacker’s ip and port to port I want to listen on.
I then opened a netcat listening session on port 4444:


Uploading the file didn’t give any errors so it was successfully uploaded. I ran it by changing the url to /uploaded_files/exploit.php and going back to the netcat session we get a reverse-shell :

After looking around, I went to the webserver directory /var/www/html and found flag.txt file but didn’t have permission to read it.
But, there is a hint.txt file, on checking it I get the 3rd flag!! :
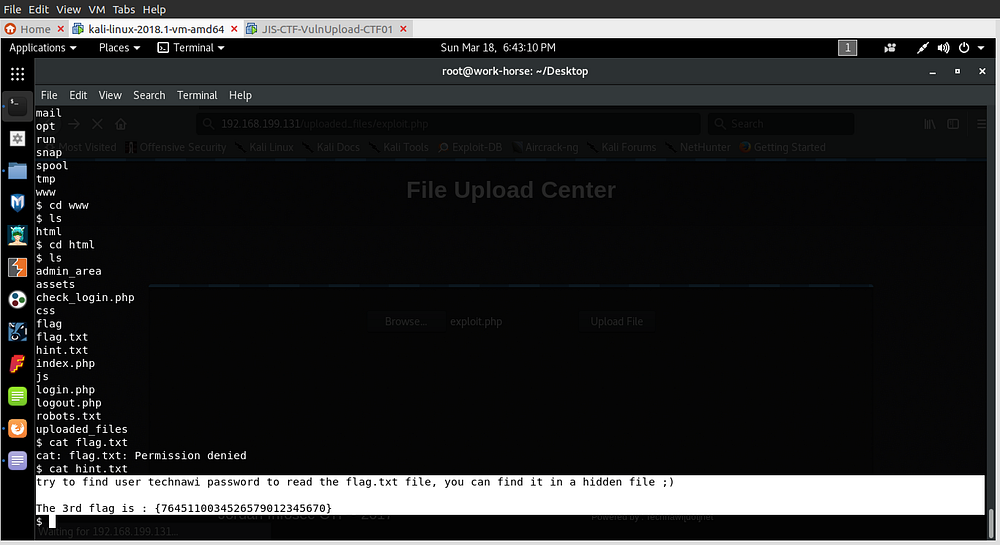
The hint there made me spend a while on there but after googling and read another writeup, it turns out the file is hidden in a secret location not hidden in a linux sense that it’s not visible.
I decided to find files that belong to user technawi and have readable content :
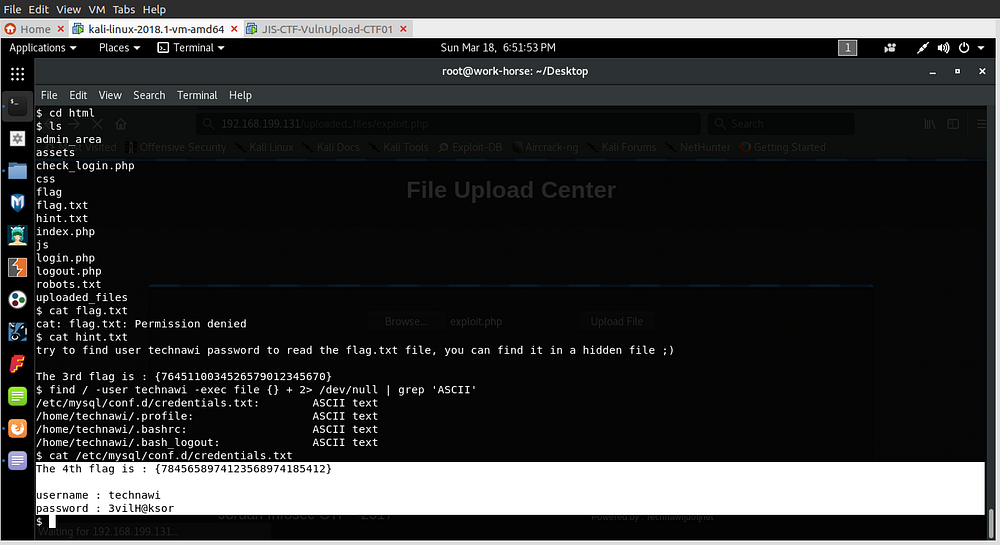
After searching I get the credentials.txt and there’s the 4th flag!!.
I used the password and switched user to technawi so that I can read the flag.txt file:

At first try the su (switch user) did not work as it needed to be run from a terminal, so using that python command I spawn a shell. However, this VM only had python3 installed so I had to use python3 to run the command. After changing user to technawi the flag.txt has our 5th flag!! which is also the last flag.
After thoughts:
It was a simple CTF challenge even for me as a beginner, even though I didn’t immediately understand the hint and had to look for help from another writeup.
I will definitely be doing more challenges like this and write about them.
