MitreCTF 2019 Writeup

This weekend my team NoPwnNoGain participated in the MitreCTF organized by MITRE Cyber Academy. It ran for 24 hours.
CTFs are a great way to learn about cybersecurity/hacking that’s why I enjoy participating in them. Depending on the areas you would like to gain skills there are many categories for you.

We solved 10 of the challenges, I’ve written about the ones I solved.
Let’s get into it.
Web
1. Super Secret Hidden Service

The url provided was https://138.247.13.115. Visiting the link we get this.
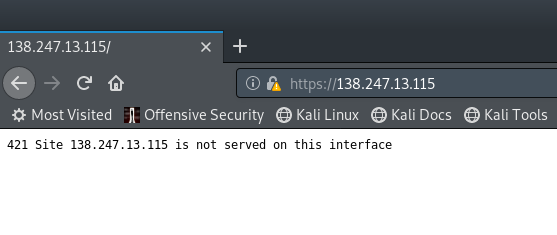
I decided to google this error and found something relevant here, https://caddy.community/t/404-site-not-served-on-this-interface/3936. It just means that the caddy service responds to the server name the client sends and because we sent the IP we get this error response, this sounds like we need to know the domain name.
So I thought to run an nmap scan and see what other details about the server I could get.

Visiting the new DNS entry that is given, we get the flag.

2. Alan Turing
This was just a simple research challenge on Alan Turing for security questions to reset his password. All the information was on Wikipedia.

Despite being an easy task I took some time on this because the answer on school was checking punctuation as well as the . after St in St. Michael’s. Got that hint from the admins.

3. TODO

Visiting the url, http://138.247.13.110/, provided we get a simple todo list app.

Let’s test it out and create an new test entry.

It’s created and looking at the url it has an id of 1000, my first thought is can we change it to get to access other entries. I change it to one and we can read other entries. So this means that somewhere in between 1–1000 is our flag.

Automation ftw! I wrote a python script to make the requests and find the flag.

It basically just loops through 1–1000 then removes the html tags with regex and checks for the flag. MCA{} is the flag format for this CTF.

After about 600 requests I got the flag.
Linux
1. Clean Room

Description
The year is 30xx. Clyde is trapped in an interdimensional transport module. The Federation has captured the module and has prepared to dock. The captain of the Federation lander has instructed the henchmen to bring Clyde in to Federation custody. As a precaution they will place Clyde in a clean room to remove any radiation. Luckily, you’ve hacked into the lander’s mainframe. Help Clyde escape!
ssh ctf@138.247.13.108
First ssh login drops into a restricted shell.

Easy bypass for restricted shell through ssh is to force a tty to use when logging in with -t option.

The flag was in the root folder.

2. Getting a head

Description
Our team has gained limited access to an important system, can you help us escalate our privilege and find the flag?
ssh ctf@138.247.13.107
After logging in we get a HackMe executable file that has the SUID bit set. This must be the way for privilege escalation. First running it gives Yadayada… as output.
Next thing is to check the strings. I notice
head /var/log/auth.logSince it’s not calling head explicitly, it is relying on PATH variable to find the file. We can abuse this.

So I created a file named head in /tmp and added bash to itand made it executable, this will just run bash when it’s executed. Since the HackMe executable has the SUID bit set we will get root once bash is called.

We can then read the flag in the root folder.
3. Linux-100
I forgot the challenge name for this one. So I just call it Linux-100 as it had 100 points.
Immediately after logging in there’s nothing in the home folder. Going to the root folder there is sudo archive present, I bet it was left there intentionally to mean sudo has been installed here.
Checking sudo permissions for our user we see he can run that vim command as root without a password.
In this situation I check gtfobins for ways to abuse this permission.
Using those commands listed, I set the shell to bash and running it drops us into a root shell. We can now read the flag.

Binary RE
I only solved the easy one on this. Not that good at Reverse Engineering.
After downloading the zip we get an executable called challenge. Running it just asks for the flag.
Next is to just check the strings, we might get lucky and find something useful like from the other linux challenge.

Sure enough the flag is present in the strings, when we feed it back to the program it acknowledges it.

Conclusion
I’m pleased I was able to solve more challenges this time as compared to the other CTF. Proof I am getting better!
For the other challenges solved by my teammate I will drop a link or update this article with those solutions.
If you read the previous CTF writeup I was solo and now it’s much better with a team, we got to top 100. If you would like to join up you can contact me on my Twitter(preferrably guys from Kenya).

