Hacking DC: 2— Vulnhub

Since this a continuing series I’ll just dive in.
Service Enumeration
First lets run a fast scan on all ports to discover which ports are open.
nmap -sS -p- --min-rate=1000 192.168.56.105
There is an unusual service running on port 7744. Let’s use nmap scripts to find out more about it.
nmap -sC -sV -p 80,7744 -oN DC:2.tcpscan 192.168.56.105
Turns out port 7744 is just running ssh. Let’s start with enumerating port 80 since ssh has low chances of being vulnerable.
HTTP
According to the nmap output, a wordpress site is running. Viewing in the browser using the ip doesn’t work, we’ll need to use a hostname. After adding an entry for dc-2 in the hosts file the website loads.

Checking the flag it hints of using cewl to come up with a password wordlist.

Before creating the wordlist let’s enumerate users using wpscan.
wpscan --enumerate u --url http://dc-2
Users found: admin, tom, jerry
Let’s create the password wordlist:
cewl -w DC2_wordlist -m 5 http://dc-2After creating the wordlist we can bruteforce using wpscan to find the valid passwords.
wpscan --password-attack wp-login -U users.txt -P DC2_wordlist --url http://dc-2
Exploitation
Now that we have valid passwords for the wordpress site we can login and find a way to exploit it. But first I will test for password reuse on ssh.
ssh tom@192.168.56.105 -p 7744
Logging in as tom works but the shell is restricted, before trying to escape it let’s try out jerry’s credentials. Unfortunately that doesn’t work maybe jerry isn’t allowed to ssh.
Escaping Restricted Shell (rbash)
Looking at the path we can see the location of binaries that are present. We can see that we can abuse vi since it is just a symlink to the original vi.

Using this commands from gtfobins we can escape the restricted shell using vi.
vi
:set shell=/bin/sh
:shellAfter escaping the shell we need to export the path variables again.

Now that we have a proper shell we can look around. According to flag3 we should su to jerry, since we have a password for jerry we can use it.

In jerry’s home directory there is flag4.txt:
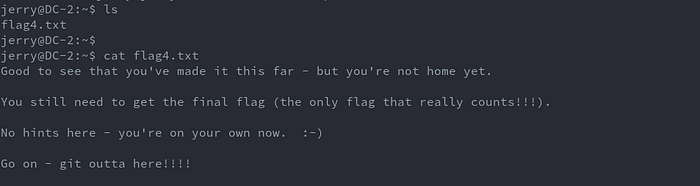
The last line is particularly interesting, maybe there is something we can do with git. Looking around we can read the bash_history file.

Jerry had previously run sudo on git, we can confirm if he has any sudo permissions using sudo -l.

Jerry can run sudo on git with no password, we can abuse this permission to get root with the following command:
sudo git -p help config
!/bin/shWe finally get a root shell and we can read the final flag.

Post Exploitation
Since we already have root permission on this box we can look around and see what other interesting information we can collect either passwords or hashes.
Looking at ssh config we see the default port was changed and only tom was allowed to ssh.


Going into /var/www/html we can read the wordpress config file (wp-config.php) for db credentials.

After logging into mysql we can get the wordpress password hashes in the wp_users tables in wordpressdb.

Since we already have tom’s and jerry’s passwords we can try crack the admins password using hashcat. I tried a few wordlists but wasn’t successful. Since I don’t have a top notch rig for faster cracking I’ll leave it at that.
Conclusion
This was a good step up from the previous box since we needed to create our own wordlist for bruteforce using cewl. A perfect VM for beginners.
Twitter: ikuamike
Github: ikuamike
