Frolic — HTB WriteUp

This box was really CTF-like when getting user, it was so unrealistic. You’ll see what I mean. Unfortunately I didn’t get root, not because it was difficult but because I didn’t try.
Getting User
As usual I begin with an nmap scan to get open ports:
nmap -sV -sC -v -oN frolic.txt 10.10.10.111
I’ll go for the webserver first.
Loading the IP with the port specified we just have a welcome page but at the bottom there’s a link: http://forlic.htb:1880.

Since nmap didn’t pick up that port it means there’s probably some routing based on the host we request. Updating the hosts file and visiting the page once more. There’s a node-red page.

Unfortunately this was a major rabbit hole, so I went back to the previous page and run dirsearch to discover directories.
dirsearch.py -u http://10.10.10.111:9999/ -e html,txt,php -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x 403
Checking the directories only admin and backup had interesting information:
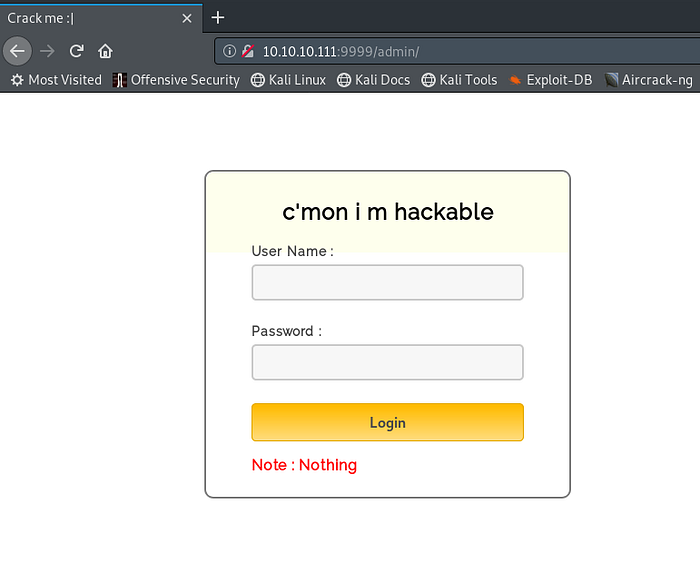


I tried these credentials to login to the admin page but they didn’t work. On checking the source of the admin page there is a login.js that contained the username and password.

username: admin
password: superduperlooperpassword_lolAfter logging in I get this:

Now the CTF begins, if you’ve done ctfs before you’ll guess it’s some sort of an esoteric language. But which one? After some researching I narrowed it down to ook! .
Decoding it on this page we get a new directory to check:

Visiting it there’s a page with what looks like base64:

When I encounter such encoding I use CyberChef in case it decodes to a file:

It shows it’s a zip file, I’ll use the terminal to retreive it:

Trying to unzip it asks for a password:
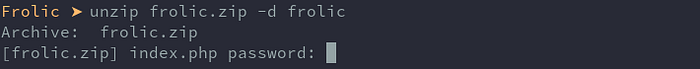
I tried the password that was in the password.txt above but no dice, so I bruteforced it:
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt frolic.zip
After unzipping there is an index.php file

index.php contents:

Some more encoding!!

The encoding is hex, so I’ll just use xxd:

Another Base64 encoding, decoding that results in another esoteric language called brainfuck:

It decodes to:

Well that doesn’t seem to help move forward, I then realized maybe I may have missed a directory and decided to do a recovery again but this time recursively. I used recursive-gobuster tool:

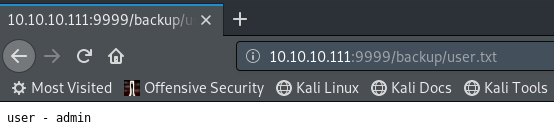
There are new directories under dev that I hadn’t checked out. Under backup there’s a new directory.
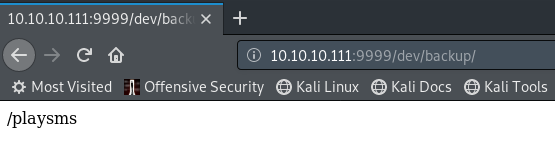

idkwhatispass must be the password after all that decoding we did to find it.

Using admin as user it works.
Exploitation to shell:
Using searchsploit to discover exploits:

There are several exploit for this service, there’s even a metasploit module but I’ll do this manually. I used this https://www.exploit-db.com/exploits/42044 to achieve RCE.
This exploit abuses the import feature on the phonebook that uploads a csv file with php.
Here’s the exploit.csv that I will upload:

The strategy is to upload the csv and capture the request with burp then change the user-agent to our reverse shell command and submit.
Browse for csv and import:

Capture request and add reverse-shell command:

Getting shell:

Finally reading user.txt:

Looking around the home folder I find a .binary folder with a file named rop that has a suid bit set. Possibly the privesc route, considering the name I assume its a rop exploit.

Since I didn’t follow through with this I will be waiting for other writeups to see how it was done.
